
Electric sector supply chains experience a whole host of threat vectors and need to be protected by a multitude of controls and processes to achieve defense-in-depth.
This article’s security focus is on the non-technical processes before equipment ever touches your network (e.g., the risk analysis of the vendor itself and coordination with the vendor on basic items such as cyber security incidents, remote access, product vulnerabilities, and product authenticity). These are basic supply chain hygiene considerations that inform high level decisions like the following:
- Should we do business with this vendor?
- If we must, what additional controls might we implement before the product connects to our system?
The ERO Enterprise vision is a highly reliable and secure North American bulk power system. Delivering reliable electricity to the end use customer is the ultimate end goal. Both Bulk Electric System (BES) and bulk power system facilities feed distribution lines to the customer and are equally important to a reliable supply of electricity. Additionally, the business health of the asset owner/operator is a consideration in the ongoing operation of the power system.
The scope of NERC CIP supply chain standards, however, is limited to the BES as defined by NERC. While NERC Critical Infrastructure Protection (CIP) Supply Chain Standards provide a baseline level of supply chain hygiene requirements for BES equipment and services, there are areas on the BES, like the remaining power system and the IT side of the asset owner/operators, that are not covered. Results from the 2023 MRO regional security risk assessment reinforced that business continuity issues at the asset owner/operator level can have power system impacts. The 2023 regional security risk assessment included questions on IT/Operational Technology (OT) isolation and how IT business continuity issues can negatively impact OT and the end-use customer. The assessment results indicate that the electricity sector does have some IT/OT integration that could create a vulnerability during an IT cyber-attack (as was the case in the Colonial Pipeline ransomware attack in 2021). Power delivery to the end-use customer also depends on other utility company support functions, such as billing, call centers, Human Resource applications, payment processing, and corporate Information Technology (IT) security.
To help you achieve better coverage of your company’s supply chain, MRO created the following chart to illustrate areas that may not be covered by your supply chain hygiene activities. (Please note that the information in this chart is not an inclusive list of all supply chain security threat vectors.)
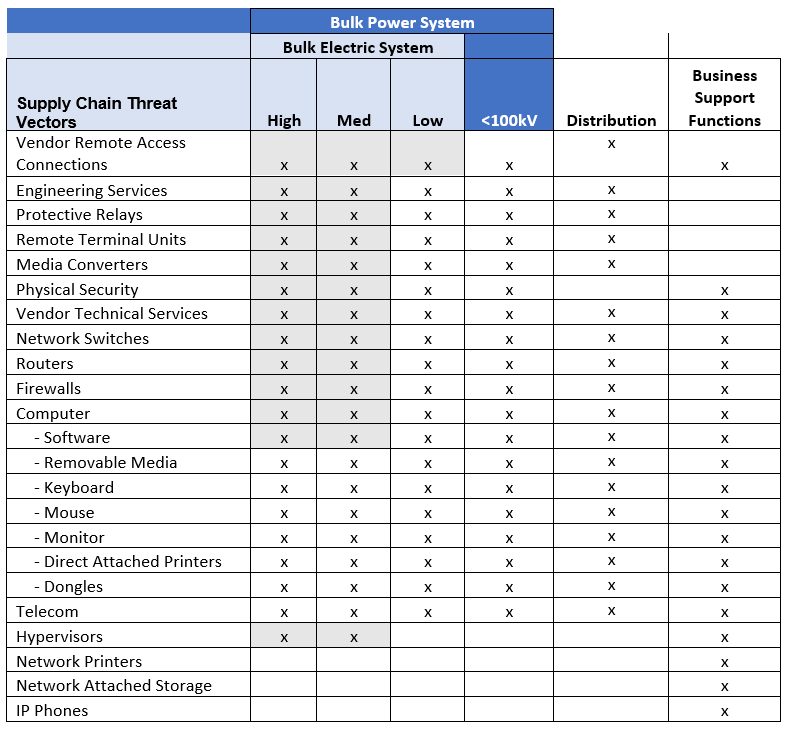
The electricity sector is one of the only critical infrastructure sectors with mandatory cyber security standards. (The U.S. federal government issued mandatory regulations for the pipeline industry in 2021 following the Colonial Pipeline attack.) As mentioned earlier, standards provide a baseline of protection against risk. Because standards are static, they cannot safeguard an organization against all risk. Protecting the power system as a whole requires security protocols above and beyond mandatory standard requirements. A key component is supply chain hygiene activity that occurs before purchasing and in-servicing equipment that is a potential cyber security threat vector. MRO strongly recommends that all procurements (for bulk power system and business support functions, not just BES required assets) be subject to a risk assessment for direct and indirect power system impact (i.e., business support functions that could propagate to the power system). The results of such an assessment will help determine your organization’s next steps. Much of the equipment that needs to be secured is ubiquitous across IT and OT. Because some equipment is already subject to mandatory cyber supply chain hygiene activities, existing security processes and programs can be leveraged to assess equipment or systems outside of the scope of mandatory standards. The chart above clearly shows that many purchases are in use across broad areas of your organization and are likely covered by supply chain hygiene requirements for some portion of the power system that you operate, so expanding coverage may be incremental for some organizations.
Standards are like castle walls and a moat…the foundation of a good defense. They address the known-known risks that are persistent and highly impactful. However, the castle also has archers who can quickly adapt and react to threats before adversaries get to the gates. The castle’s security strategy also includes archers that address threats that standards alone do not by actively hunting targets more forward in the risk continuum. An in-depth strategy has the operational mission and flexibility to reach beyond the castle walls.
– Lee Felter, Principal Security Engineer, MRO